1:36nihhatya dhārtarāṣṭrān naḥ kā prītiḥ syāj janārdanapāpam evāśrayed asmān hatvaitān ātatāyinaḥ1:37tasmān nārhā vayaṁ hantuṁ dhārtarāṣṭrān svabāndhavānsvajanaṁ hi kathaṁ hatvā sukhinaḥ syāma mādhava In Śloka 36 and 37, Arjuna
READ MORE
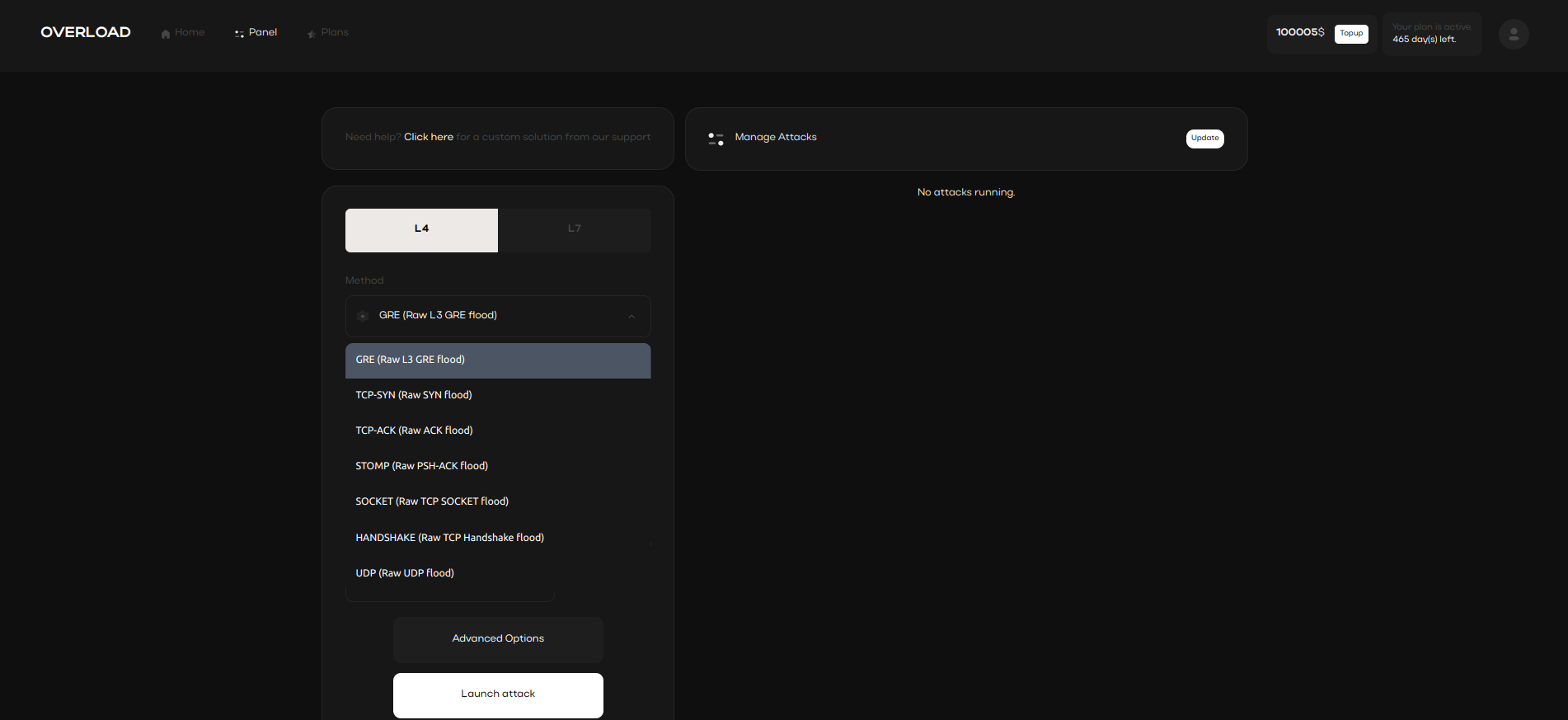
Stresser tools with IP spoofing capabilities obscure the attacker’s identity,
preventing detection and enabling secure, concealed testing. IP spoofing aids in masking attack origins,
adding a layer of anonymity during cyber evaluations.
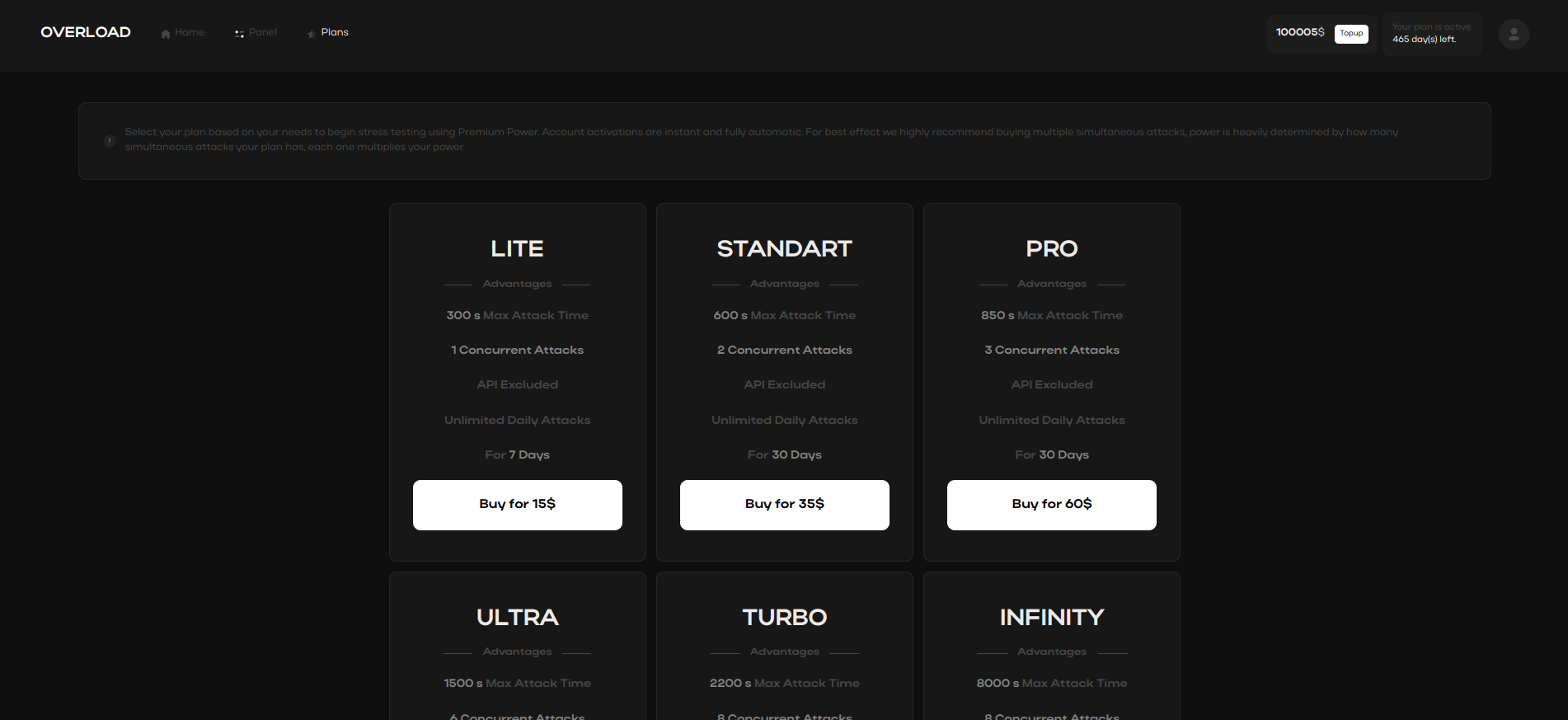
Through strategic load testing, booter tools expose vulnerabilities and system weaknesses.
They reveal weak points in server infrastructure, helping organizations preemptively reinforce their cybersecurity defenses.

Grabify tools are designed to monitor and analyze traffic patterns.
They support cybersecurity measures by identifying potential threats and aiding in incident prevention.

Layer 7 tools analyze application behavior under stress, providing insights into scalability
and enhancing user experience.
No Schedules for this section.
Spiritual tour
Date & Time : 24-02-2026 - 07-03-2026
Venue : Pancha Dwaraka Yatra
Contact Person : Admin
Contact Number : 9497033111



